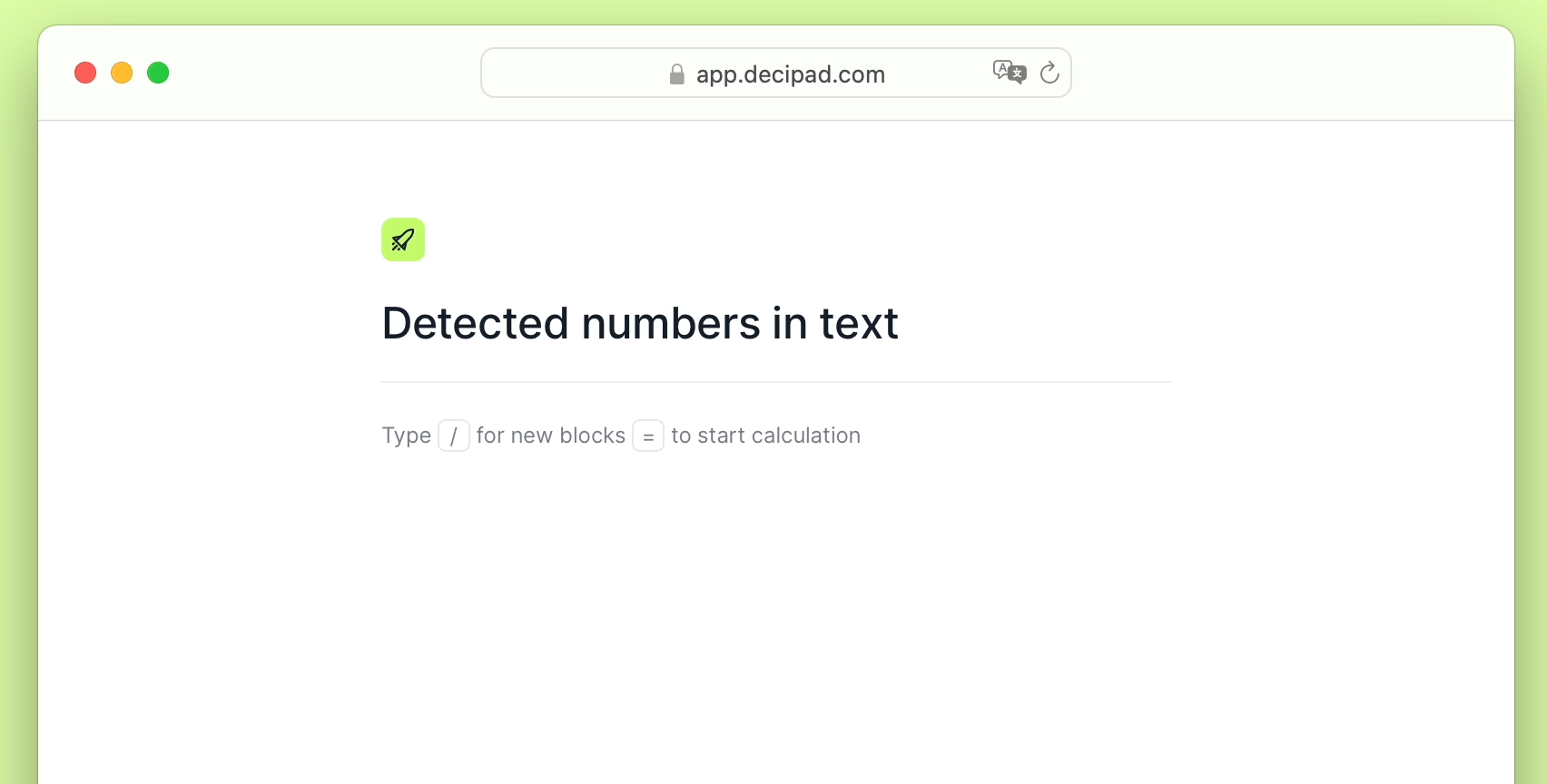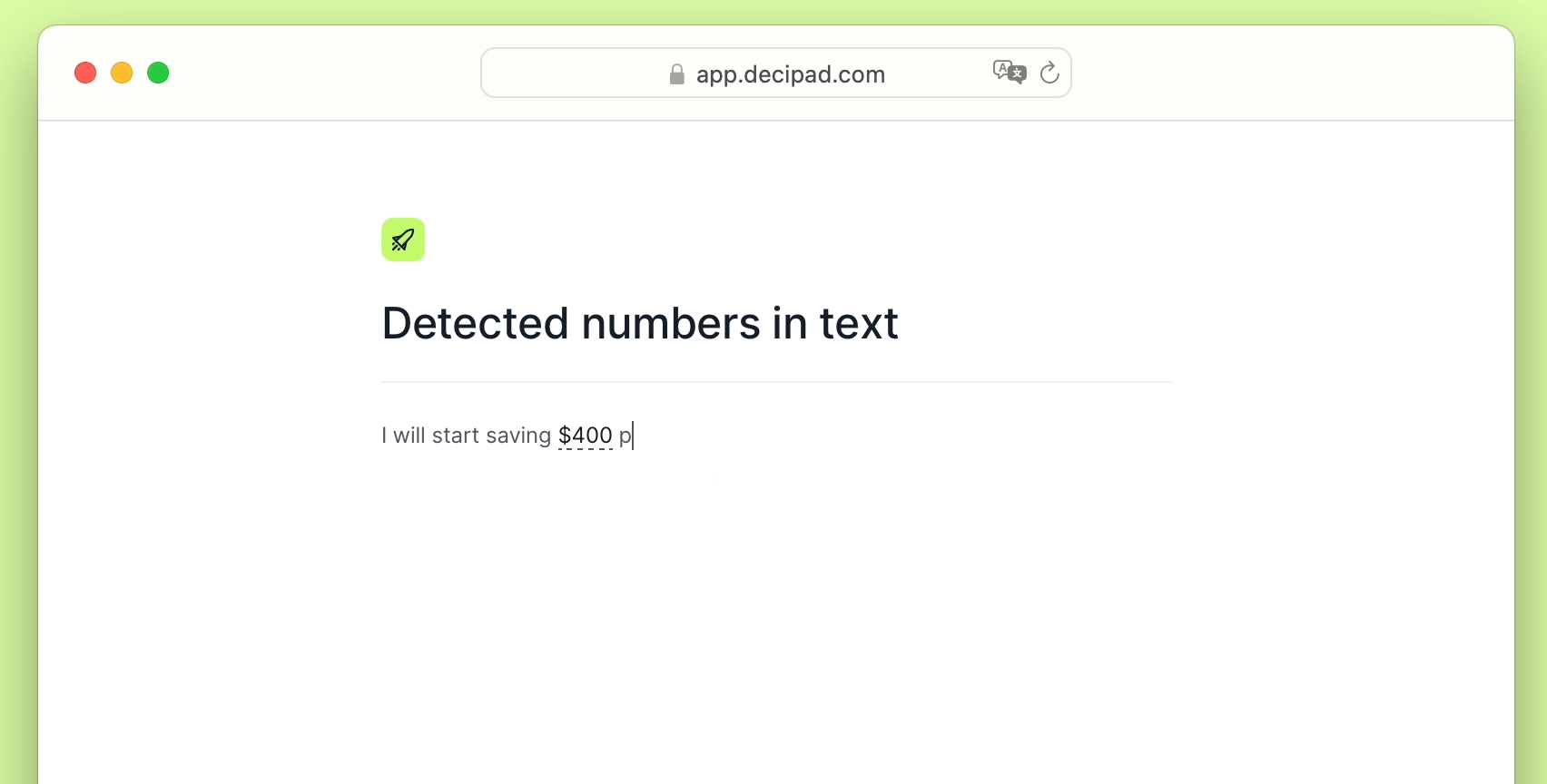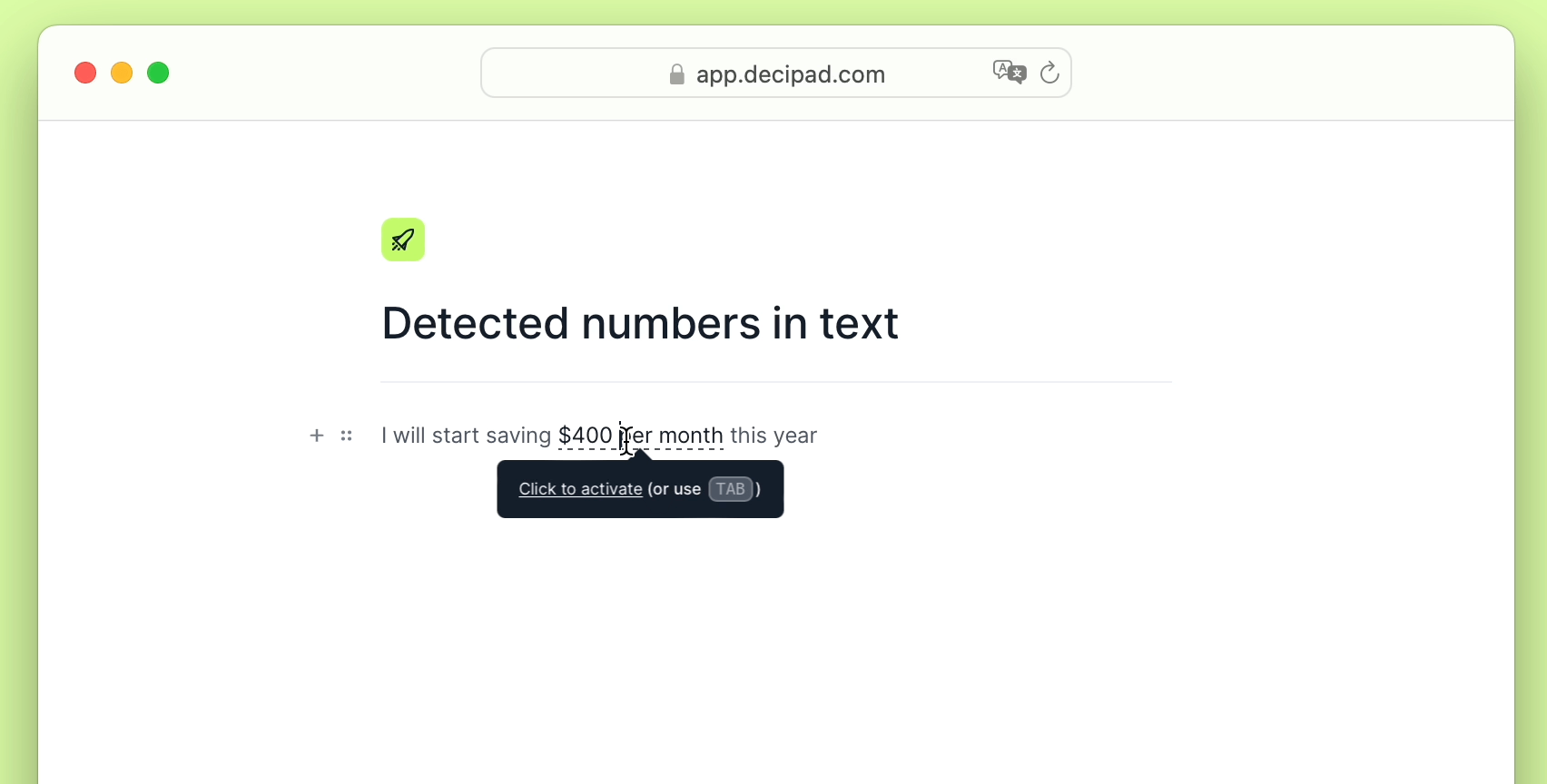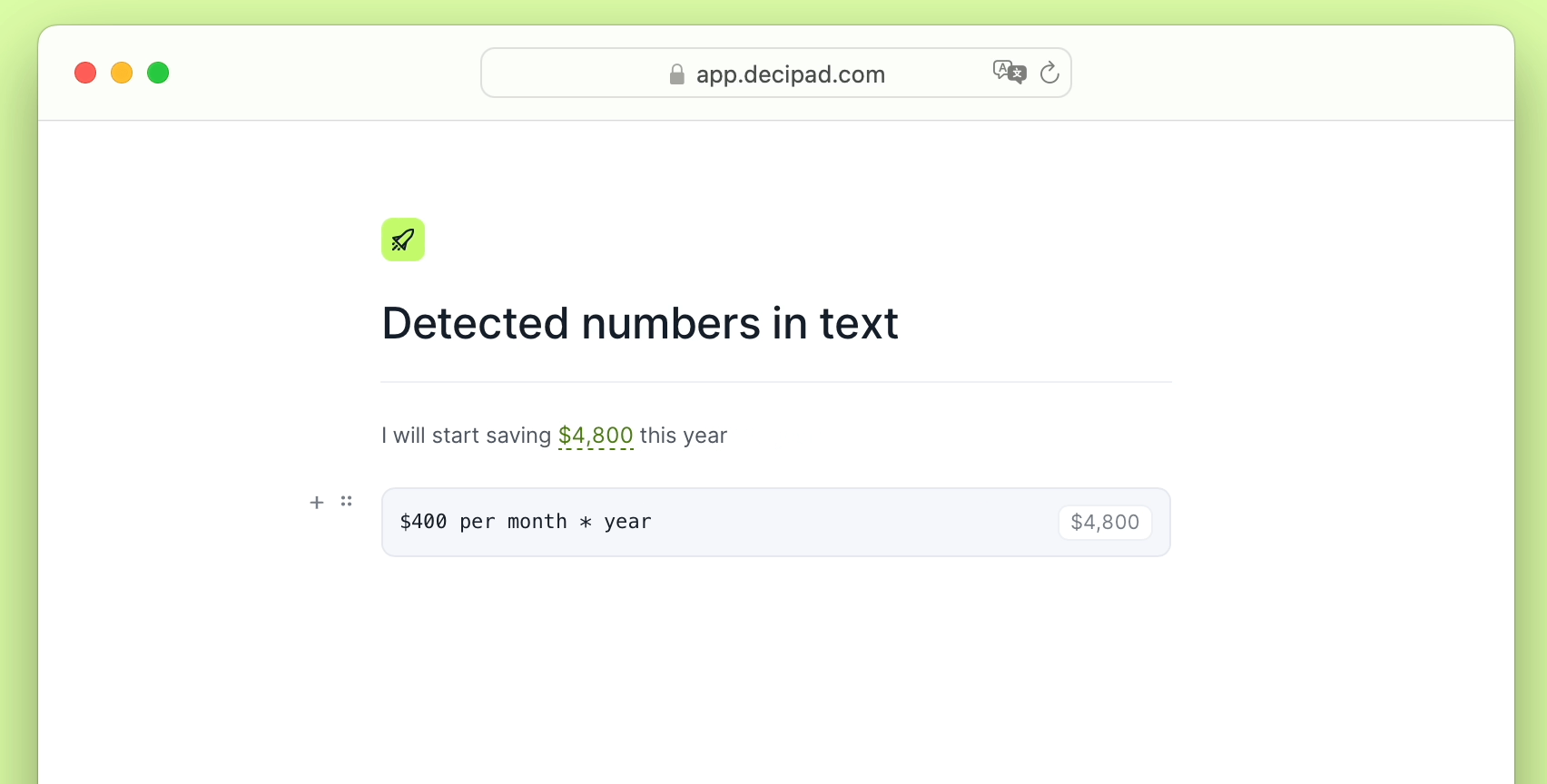
Simple Tips About How To Detect Conflicker

The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139.
How to detect conflicker. Skip this and learn how to remove downadup and conficker! Later that year, the conflicker worm pushed the dga tactic into notoriety. However, there is a free, easy way to detect and remove it:
The downadup, or conficker, infection is a worm that. Even after 10 years, it is still. The conficker worm is a malicious code that made use of a software vulnerability in windows computer network coding.
5 the latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm. 6 answers sorted by: Conficker, as of this writing, is nearly eight years old, and almost every antivirus available today can detect and quarantine the worm before it spreads.
The output looks like this: Refresh the page, check medium ’s site status, or find something interesting to read. Run the malicious software removal tool from the microsoft malware protection center.
Conficker was first detected in november 2008, and is one of the most widespread worms that infects machines running windows os. 500 apologies, but something went wrong on our end. Run the malicious software removal tool from the microsoft malware protection center.
Security event logs network monitoring tools firewalls with logging (i.e.,. Checkall if set to 1 or true, attempt to communicate with every open port. What is downadup and conficker?
./scs.py 127.99.100.2 127.99.100.2 seems to be infected by. There are a few tools that you can use to track and find conficker infected computers on your network. Read microsoft's information on how to remove.
Later that year, the conflicker worm pushed the dga tactic into notoriety. Even after 10 years, it is still possible to find conflicker or one of its variants on some of. Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008.
Checkconficker if set to 1 or true, the script. The first known malware family to use a dga was kraken in 2008. How does the conficker virus work?