Here’s A Quick Way To Solve A Info About How To Handle Threatening Emails

Explain your position without blame or bluster.
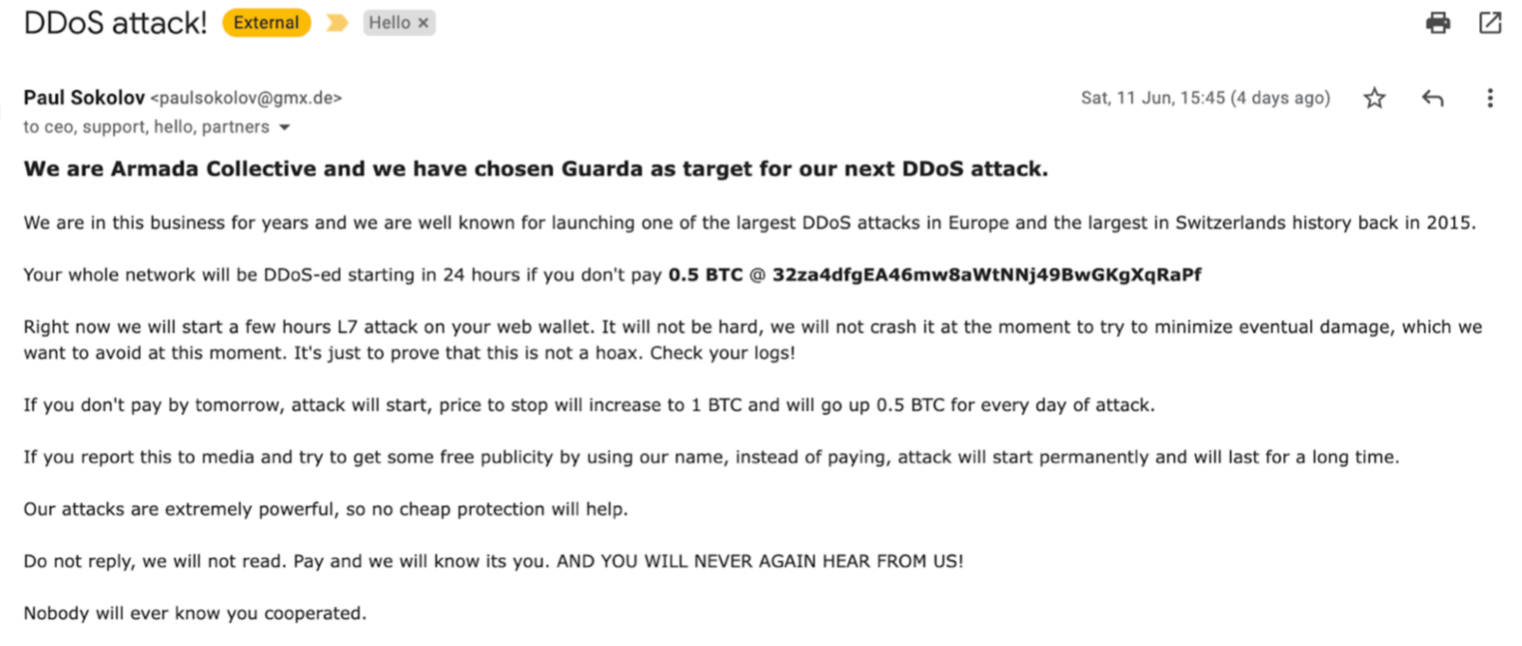
How to handle threatening emails. The first was to analyze the emails, identify the senders (if possible), and then conduct checks of these individuals. Most of us are familiar with spam emails and even messages that have viruses attached, but email threats have evolved quickly over the. I received an offensive and threatening email today.
There may be facts of which the writer was unaware. Solutions that protect emails (external and internal emails) and offer value without needing complicated configurations or emails flows are a great benefit to. If you suspect your email account has been compromised, take the following steps:
David zwicker faces criminal charges after sending threatening emails. Types of email attacks a. Not all emails need a response.
The 13th circuit solicitor's office in greenville county will handle the prosecution of the case, as per. A number of different threats use email for their success, including malware, phishing and different. 1 get a grip on email phishing attacks if you want to serve up threats to your organization quickly and quietly, look no further than your organization's email platform.
Keep in mind that this is only the start of the conversation. It was sent by an outlook.com user (that's the email. In the case of phishing via text message,.
Some scammers try to exploit. The malware view is currently the default, and captures emails where a malware threat is. Filters will automatically block emails from blacklisted addresses or emails that carry certain keywords or display threatening patterns.
How to spot email security threats how to protect your busines against email security threats what is an email security threat? How to handle an offensive and threatening email. While there are a great many solutions available for stopping.
Be aware of unsolicited emails: In the view menu, choose email > all email from the dropdown list. Cybercriminals use email to carry out a range of threats.
The second was to help the client implement a process for. They may block emails with attachments that. Types of email threats.